We’ve written before about how important security is in today’s online world, like how password security is not optional and some browser dangers to know about.
But there are a lot of potentially confusing terms that float around. Let’s define some of the most common and important security terms everyone should be familiar with.
1. 2-Factor Authentication
Two-factor authentication is one of the most important ways of adding additional security to an account. In addition to something you know (your password), it requires something you have (a code from your phone, or a physical security key) to log in. Read more about why two-factor authentication is so important.
2. Adware
A type of malware (see below) that primarily exists to barrage the user with advertisements. Common when you search the web for “free” software.
3. Botnet
A botnet refers to a group of computers under control of an attacker. Owners of the controlled computers usually have no idea they’re being controlled.
With the power of multiple machines, an attacker can use a botnet to send large amounts of spam, or perform a distributed denial-of-service attack (see below).
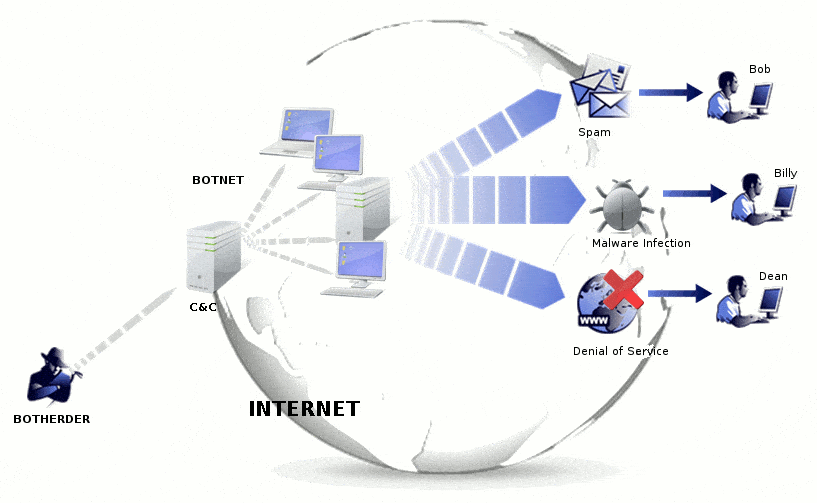
4. Denial-of-Service Attack
A denial-of-service attack (DoS attack) occurs when an attacker tries to make a service unreachable to legitimate users by flooding it with illegitimate requests. Often, this comes as a distributed denial-of-service attack (DDoS), where many different sources create the flood of traffic.
DDoS attacks can temporarily shut down websites, credit card payment services, and similar. When a server suddenly receives millions of requests per second, it simply can’t keep up with the traffic. This is similar to a large group of people cramming the door of a store so that normal customers can’t get in.
5. Encryption
Encryption is, at its core, encoding information so people who aren’t authorized to see it have no way to access it. Learn more about encryption in our primer.
6. Exploit
An exploit is a way to take advantage of a vulnerability in software. Typically, software updates patch these vulnerabilities, which is why it’s so important to update both your software and OS.
7. Firewall
A firewall is a barrier that shields a device or network from dangerous traffic. It allows you to filter what kind of traffic can come in and go out of a network. Firewalls can be either software (like the built-in Windows firewall) or hardware.
8. Hacker
A hacker is someone who seeks to exploit computer systems. Typically, you’ll hear about white-hat and black-hat hackers. A white-hat hacker is honest and works with companies to find and address vulnerabilities before someone malicious can. Meanwhile, a black-hat hacker tries to exploit vulnerabilities to make money or similar.
9. Malware
Malware (a combination of “malicious” and “software”) is a catch-all term for dangerous programs. It encompasses viruses, worms, Trojans, spyware, and other sorts of nasty software.
10. Phishing
Phishing is an attempt to steal personal information by masquerading as a legitimate entity. Often this involves a fake email that appears to come from your bank, Apple, Google, etc.
It claims that you need to confirm some information by clicking a link, but doing so takes you to a fake website. If you enter your info here, you’re handing it over to attackers.
11. Ransomware
Ransomware is a type of malware that encrypts all the files on a computer and demands payment to unlock them. If you don’t plan for a ransomware attack, this can be devastating.
12. Spam
Spam refers to unwanted content online. Usually this means email spam—junk messages for shady products and other nonsense. Spam is relatively harmless, but often includes links to dangerous websites.
This term can also refer to repeated low-quality comments on websites, using dishonest tactics to boost your rankings on Google, and similar.
13. Spyware
Spyware is a type of malware that, as it sounds, is designed to spy on the user. Due to its nature, spyware usually hides out of view and collects data about the user’s computer and what he does. It then sends this data to another server, perhaps to build advertising.
14. Virus
Once used as a catch-all term for dangerous software, a proper virus is a type of malware that spreads by infecting other files. This contrasts with other forms of standalone malware.
15. Zero-Day
A zero-day vulnerability is one that the software developer or manufacturer isn’t aware of. A zero-day attack then, is something attackers launch to exploit a vulnerability before the company even knows about it.
Because no user has received a patch on “day zero”, the vulnerability will almost always succeed. Thus, these attacks are quite dangerous until they are patched.
Brushing Up on Security
Now you know 15 major security terms. Of course, these aren’t the only important ones, but they’re a good introduction. The more you know, the better you can stay safe.

