Every website you create an account with requires at least a username and password. Since passwords are sensitive information, what measures do websites take to make sure your password doesn’t fall into the wrong hands?
As it turns out, this is an important topic because of the security breaches that happen all too often. Let’s take a look at the wrong way to store passwords and dive into modern security methods that keep this info safe.
Storing in Plaintext: A Big No-No
Some terribly insecure websites store your password in plaintext. That means exactly what it sounds like—your password is as plainly readable as the words on this page. As you can imagine, this is wildly unsafe because if the company’s database is breached, the attackers have instant access to every password. It doesn’t matter how secure your password is; any password could be stolen in plaintext form.
Hopefully, any websites still following this awful practice will improve it before long. But until then, thankfully, you can often tell when a website stores your password in plain text.
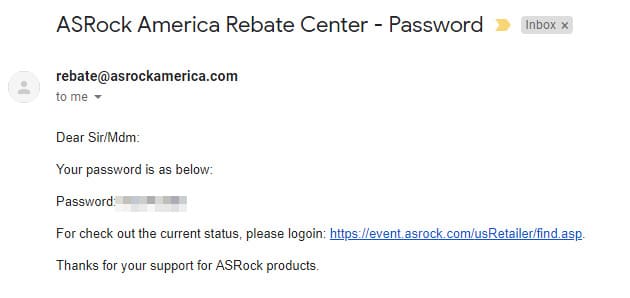
If you receive an email that contains your username and password after creating an account, that website has extremely poor security, as it’s keeping your email in plaintext. A similar case occurs if you follow the Forgot password link to reset your password and the website emails your password to you. A website should never know your password. This is why when you reset your password, sites send you a link to set a new password instead.
There is one exception to this: temporary passwords. Sometimes, a website may send a temporary password to you as an extra security measure. This is a suitable practice, and does not mean that a website is storing your actual password in plaintext.
To see how common plaintext password storage is, check out the blog Plain Text Offenders to see many examples of websites sending their users plaintext passwords. This also illustrates services to avoid.
How About Encryption?
If you’ve read our introduction to encryption, you might think that it’s the answer to the plaintext password problem. After all, encryption takes readable data and scrambles it into something nonsensical unless you have the key, so it sounds like a good solution. And while that’s partially right, encryption alone is not enough to protect your passwords.
Encrypted data is unreadable without the key. For instance, if you encrypt your computer and lose the encryption key, you’ll have no way to recover the data. However, whoever possesses that key can access all the encrypted data. Therein lies the issue with using encryption to protect passwords.
Websites constantly have to check to make sure what the user entered matches the password they have on file for that person. This means that it has to keep this encryption key handy for frequent use. That key is thus a prime target for hackers. If exposed, an attacker could decrypt every password with it.
This is known as “reversible encryption” and is not considered a safe way to store information either.
Introducing Hashing
Hashing is a more powerful form of encryption, because it can only be performed in one direction. There are many different hash functions for taking plain data and scrambling it. The transition from password to hashed data is easy, but reversing it is extremely difficult.
Thus, your password of MyPassword12# might become Gh1s09*zH61?K when hashed. This allows a website to run the same hashing function to authenticate your password every time you log in. And if someone broke into the database, they would only have a useless string of numbers.
However, this isn’t perfectly secure. Because the hashing function doesn’t change, the same password will always produce the same hashed value. Due to this, hackers have devised tools known as hash tables and rainbow tables for breaking hashed password values.
Hash tables are tools for cracking weak passwords. They’re essentially a giant list of common passwords, all hashed with the same function. An attacker can search the table to easily reverse-engineer your password.
As an illustration, say you use the poor password of mypassword on a website, and that hashes to PzMq10&%Rp. An attacker could simply look up that hashed value in a hash table to find your password.
Rainbow tables are used to crack more complex passwords. The details are too complex to discuss here, but they essentially use advanced functions to check huge numbers of possible passwords. It takes a lot of computing power, but it can eventually crack passwords.
Finishing With Salt

As we’ve seen, each increasingly secure step adds methods to combat issues with the prior one. We finally arrive at salted hashes, which prevent the cracking methods discussed above.
In essence, a salt is a large amount of random data added to a password before it goes through the hash function. The salt is different for every user, meaning that even identical passwords have different hashes.
This is crucial, because it prevents hash tables and rainbow tables like described above. Hackers can no longer be sure that every PzMq10&%Rp hash corresponds to mypassword. Because of the salt, that weak password becomes something like mypasswordYma0RX419Xm38E, which is not likely to appear in hash tables.
Websites store the salt along with the hashed password value in order to authenticate it in the future. But even if an attacker broke into the database and stole both the hashed password and the salt, they would still have a hard time cracking the password. This would require coming up with a table for every individual salt value, which would require a huge amount of effort.
Finally, some websites are starting to use slower hashes to increase security. Hashing passwords quickly is convenient for the user, of course. But with slow hashing, cracking passwords becomes less attractive to attackers. They can run fewer computations per second, meaning that every cracked password takes longer. Thankfully, it results in little difference for the user.
Password Security Is Still Vital
We’ve taken a tour of the various methods websites use (and shouldn’t use) to protect your passwords. Now you know what’s going on behind the scenes when you enter a password and the website lets you in.
It’s important to remember that the attacks we discussed above are only part of the password security equation. Even if a website uses rock-solid security (not all do), using a strong password still deters attackers if they manage to break in. You don’t want your password to be the first one cracked during a breach.
Don’t forget that despite all these security measures, a password can also be stolen through other means. If your password is your dog’s name and your birthday, anyone who knows you could probably guess it without even knowing what a hash table is.
This is why we strongly recommend you use a password manager. These let you create strong, unique passwords for every website and securely store them on all your devices.



