If your company uses Microsoft Entra ID (formerly Azure Active Directory) to manage its users, a new option for admins will push greater security onto your users. Let’s take a look at what this means and how this setting works.
Microsoft Gets More Secure
We’ve discussed before how a password alone is not enough to protect an account. Across Microsoft Entra ID, the company is pushing for greater security to protect against modern threats that can get around weaker security options.
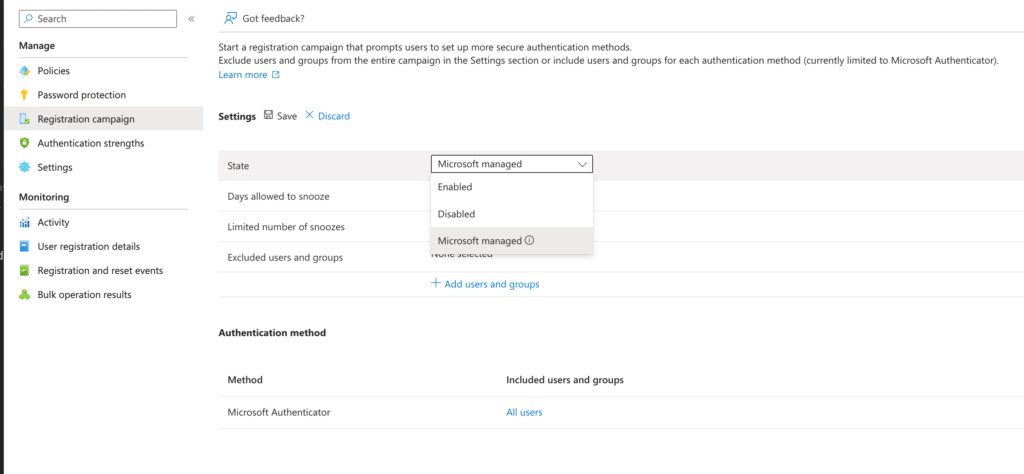
Recently, Entra ID added a setting to run a “Registration campaign” to improve users’ security. This allows administrators to force users to set up stronger security methods, or use the “Microsoft managed” options to follow the company’s recommendations. These will adjust based on the current threats in the security landscape.
If enabled, upon the next sign-in, every user will see a prompt to set up a more secure authentication method on their account. To give people time to adjust, IT admins can choose to set a “snooze” period—a set number of times, or period of days, that a user can skip the process before they’re forced to add a better security method.
In case your security needs differ for various people, you can exclude certain users or entire groups from this policy, if desired.
Not All Authentication Methods Are Created Equal
While two-factor authentication is leagues better than a password alone, even the extra security of two-factor authentication (2FA) isn’t a sure thing, since not all methods are created equal. Two-factor authentication codes being sent to email is a weak option, since email is not a secure messaging method and a person’s inbox could be compromised.
SMS texting isn’t secure either. One form of SMS phishing, for example, is social engineering: a malicious person will trick someone into giving them a security code sent to their phone.
Another growing weakness of using SMS texts for 2FA is simjacking. This is an attack where someone contacts your mobile provider (like AT&T or Verizon) and, pretending to be you, they ask the company to port your phone number to a new SIM card. If the carrier’s staff doesn’t suspect something is wrong, then all texts and calls start going to the SIM card the attacker controls.
The risk is even greater if you’ve reused passwords across sites. Plus, with this access, the malicious actor could make calls and send messages pretending to be from you.
That’s why Next7 IT’s best practice is to use a strong 2FA method, such as an authenticator app (like Microsoft Authenticator) or a physical hardware key. Authenticator apps use time-based one-time passwords, which means they change on a regular basis and are thus much harder to steal. And physical keys have the obvious advantage of being on your person, so they can’t be compromised over the internet.
Should You Force Users to Enable 2FA?
While increased security for everyone is a good idea, many businesses face challenges with adoption. For example, a company that uses a BYOD approach might have employees who refuse to install an authentication app on their own phones. If staff have concerns about the authenticator app tracking sensitive data, they should rest assured that these apps don’t expose any sensitive data, including their location information. These apps simply store secret numbers that regularly generate new login codes.
The right approach won’t be the same for everyone, which is why Microsoft gives you the option to pick. Generally, an authenticator app is a good middle ground between security and convenience. Everyone has their phones with them, so it’s not something easily forgotten like a physical security key. Many authenticator apps will send the user a prompt that they tap to log in, which is easier than typing a code.
It’s important to be aware of this option so that your users aren’t surprised by a message to add security measures they weren’t aware of. While you’re thinking about this, it’s not a bad idea to advise people on how to keep their Microsoft 365 accounts secure, too.




