In mid-August 2023, security company Cofense published a report detailing a new string of phishing attacks against an otherwise unnamed “major Energy company based in the US”. These attacks rely on the use of a QR code, which is not a particularly popular method for such schemes.
Let’s look at the details of these attacks and what you can do to stay safe from them.
The QR Code Attack
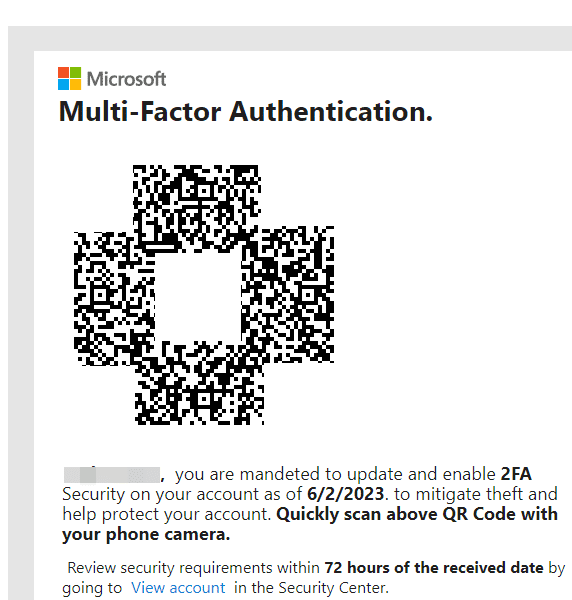
Cofense’s report on this issue explains how it works. Potential victims receive an email with an image or PDF attachment, claiming that their Microsoft account’s security details need to be updated. To facilitate this, the malicious email provides a QR code that the user is supposed to scan. As you’d expect, this code doesn’t take the recipient to their Microsoft account settings, but rather a phishing page to steal that information.
The report states that it’s seen a huge increase in incidents over the last few months. Given that other sectors like manufacturing, technology, and insurance have also been targeted, it’s important for all businesses and employees to be aware of this across industries.
How Does the QR Code Phishing Work?
If you know about the most common types of phishing emails, this setup should set off alarm bells. The difference is that while phishing emails typically try to trick the reader into clicking a phony link, this one uses a QR code to hide the trick. There are a few reasons for this.
First, email security systems can’t scan the contents of a QR code as easily as a link. Even if the QR code contains a link that’s known to be dangerous, it won’t be detected.
Second, it’s easier to disguise a link embedded in a QR code. Cofense’s report explains how the codes use Bing redirect links to bring the user to the fake page. In the example below, you can see how the link appears to be a legitimate Bing URL, but includes extra parameters at the end that load the attack website.

Redirect URLs are a legitimate way to, for example, keep track of where people clicked on a link for marketing purposes. This is a misuse of the technology to make people think they’re going to a legitimate Microsoft page.
Finally, another advantage of this attack setup is that the victim will scan the QR code (and thus visit the scam site) using their smartphone. An employee’s phone is much less likely to have robust phishing protection compared to their work computer, making the attack easier to carry out.
Thus, even though QR codes require more work from the victim and are thus not as efficient for the scammer, this method gets around many of the most common protections against these attacks.
How to Protect Yourself From QR Code Phishing
Even though this is a different type of phishing attack, the steps to stay safe are mostly the same as other phony email campaigns like this.
Most importantly, you should never trust links or any other interactive elements in emails. There is no good reason to scan a QR code in an email, especially if the message specifically asks you to. While there are apps and websites that let you see the destination of a QR code, it’s safest to avoid it entirely.
Phishing attacks masquerade as security notifications because they want the potential victims to take immediate action, without thinking it through. If you think there might be a problem, visit that account page directly in your browser—links are too easy to fake and you should never trust them in emails.

Looking at the examples from Cofense, you can also see several examples of poor grammar and wording. While these aren’t present in all attacks, poor English is a common sign of phishing. (Notice the use of “CELL PHONE CAMERA” in all caps in the second image, and the “mandeted” typo in the first.) Legitimate companies rarely, if ever, make huge wording mistakes like this.
This example illustrates how corporate anti-phishing tools and security scans aren’t enough to block every threat. Making sure all users know how to spot the signs of phishing is vital.
QR Code Attacks: Here to Stay?
It’s not clear why malicious actors have started using QR codes to run phishing campaigns in this way. They might figure that people are more willing to scan QR codes, due to these becoming more common for restaurant menus and the like during the pandemic.
Given how much these attacks have ramped up in mid-2023, it’s possible we’ll see them become more common and sophisticated before long. In the meantime, it’s not bad to check in and make sure your Microsoft account is secured.




