We’ve mentioned how important password security is before. And while having one of your accounts breached is a scary occurrence, you might wonder how it could actually happen. Chances are that a hacker wouldn’t target your account since you’re not famous or rich, right?
Well, hacking isn’t the only way to steal passwords. There are several other methods someone could use to discover and steal the password to an online account, your phone, or other important credentials. Let’s look at some of the most common.
1. Guessing
We start with the most low-tech method of all: simply guessing or figuring out someone’s password.
If your password is something that’s really simple, someone might guess it because it’s so obvious. This is why you should stay far away from the world’s most common passwords. Many publications share lists of the worst passwords annually; it’s amazing how many people still use “123456” or “letmein” as their password.
There’s another side to this. If you use a password that’s connected to you personally, someone who knows you might be able to deduce it. For example, say your password is your dog’s name and the year of your birth. If you’ve shared this information on social media, there’s a fair chance someone could figure out your password.
2. Brute Force
Another common method of stealing passwords is a brute-force attack. This occurs when a computer program rapidly runs through every possible combination of passwords until it figures yours out. While this would be extremely tedious for a person to do, software for the purpose is readily available.
While this might make it sound like every password is only a few minutes away from being cracked, the good news is that brute-forcing complex passwords would take quite a long time. The more characters your password is, the harder it is to crack.
As an exaggerated example, let’s say that your password is only one character long. If someone wanted to break into it, they would only have to try 26 letters, 10 digits, and a handful of symbols before they figured it out. A person could do this by hand in a few minutes.
Now imagine that your password is 10 characters long. It would take someone forever to manually try every possible combination of letters, numbers, and symbols. It’s a similar idea with brute-force software, but obviously computers can do much more than humans in a shorter time.
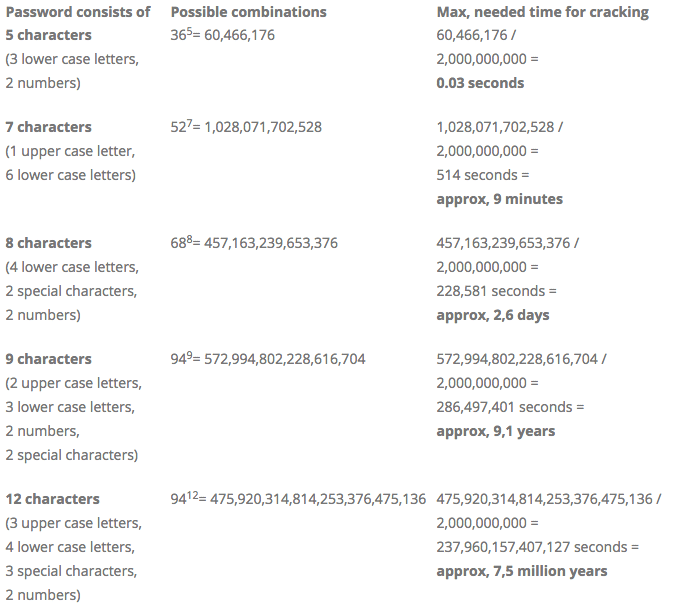
A long password is inherently more secure than a short one. Mixing uppercase and lowercase characters, plus adding symbols and numbers, helps make it harder to crack too.
3. Phishing
Unfortunately, no matter how secure your password is, it’s not of much use if it falls into the wrong hands. Phishing, which refers to a impersonating a legitimate entity to gain access to private credentials, is one way criminals steal people’s passwords.
You’ve probably seen a phishing email before. It usually contains an “urgent” message claiming to come from a bank, PayPal, or similar entity. To tempt you into clicking the fake link, it says that due to suspicious activity on your account, you need to verify your password. If you click on the link and enter your credentials, you’ve just handed them over to scammers.
You can protect your password from these attacks by not clicking links in emails. If you receive a message from a website like this, open that site manually in your browser and review your account settings. Do not trust an email link.
4. Breaches

Sometimes your password can be compromised through no fault of your own. Websites suffering a security breach is something that happens too often. And when it does, your personal information could be leaked into the wild.
If a website takes proper security measures, security breaches should only reveal hashed passwords, which are difficult to reverse-engineer. However, sometimes companies neglect to secure your information properly, and end up leaking passwords and other crucial info in these breaches.
An easy way to see if you’ve been hit by any major breaches is visiting the free Have I Been Pwned? website. Simply enter your email address and you’ll see all the breaches your email address was found in. You can use the Notify me tab at the top to get an email when a new breach occurs, too.
If you find that your information was compromised in any breaches, you should change your password for safety. Don’t forget that if you use that password on other sites, whoever stole it might try logging into other accounts too. This is why it’s vital to use a unique password for every site.
5. Spying
Snooping is yet another method for stealing a password, and comes in a few forms. For one, someone could fairly easily look over your shoulder while you enter your phone’s passcode to learn it.
If you use a pattern lock on Android, it’s also possible for someone to look at the fingerprints on your screen showing where you swiped it. This would give them a pretty good idea of your pattern code.
A slightly more high-tech version of spying can also capture your password. If installed on your computer, keylogger software records every keystroke you make for the attacker to view. This makes it easy for them to see what you typed into the password box on any website.
Thus, it’s wise to be aware of your surroundings. And running regular anti-malware scans can make you aware of keyloggers.
Keep Your Accounts Safe
We’ve looked at five common ways passwords are stolen. They range from high-tech to low-tech, but any of them could result in someone breaking into your accounts.
Of course, these aren’t the only methods of password theft. As another example, someone could figure out the simple security questions that many websites use (like “what was the name of the first street you lived on?”) and use that to reset your password.
The most important way to protect against all these attacks is using a unique password for every site. That way, even if one gets stolen, your other accounts are still safe.



