Browser extensions are a handy way to add more functionality to your favorite browser. And while there are a ton of them available, it’s wise to exercise restraint in what you install.
Let’s take a look at why you should be careful with browser extensions, and the potential risks they pose.
Understanding Browser Extension Permissions
When you install an extension in your browser, it needs access to certain areas to work as designed. You’ll see a prompt to approve these permissions when you install them.
For example, here’s what Chrome shows when you choose to install an extension from the Chrome Web Store:
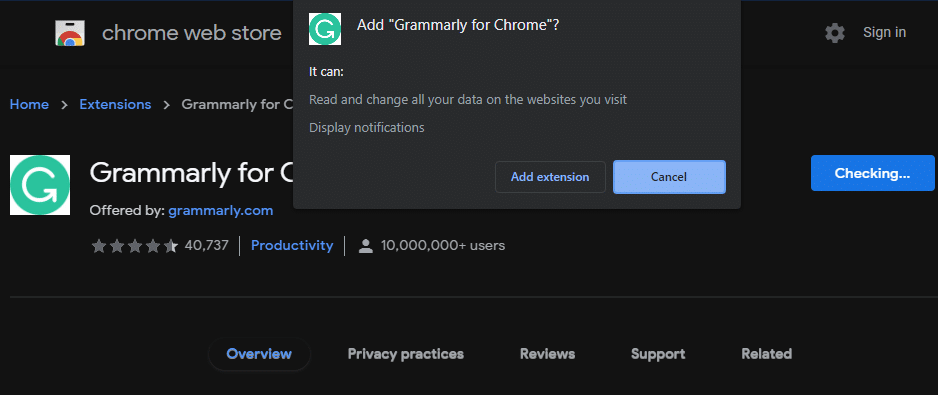
If you want to check the permissions for an extension you’ve already installed, click the puzzle icon at the top-right of Chrome and choose Manage extensions. Then, click the Details button on the extension you want to learn more about.
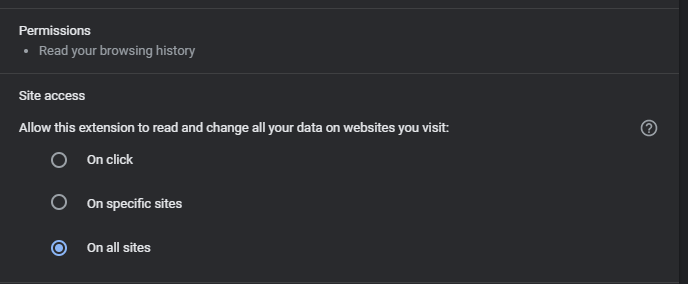
On the resulting page, you’ll see a Permissions section that lists what the extension can do. There’s also a Site access portion, where you can choose which sites the extension can run on (if it’s requested to run on many sites).
This setup is similar to smartphone permissions; both Android and iPhone have a system that requires apps to ask for access to sensitive areas like your device microphone and camera. However, on mobile platforms, you can deny any permissions that you aren’t comfortable with granting.
Browsers don’t have this level of granularity. You can tell an extension it’s only allowed to run on some sites, but that significantly limits its usefulness. For the most part, extension permissions are all-or-nothing.
Browser Extensions Require Invasive Permissions
Sometimes, an extension will only need minor permissions. For example, an extension designed to add more functionality to YouTube might request permission to read and change data only on youtube.com. Some might request to send you notifications. These behaviors aren’t necessarily dangerous.
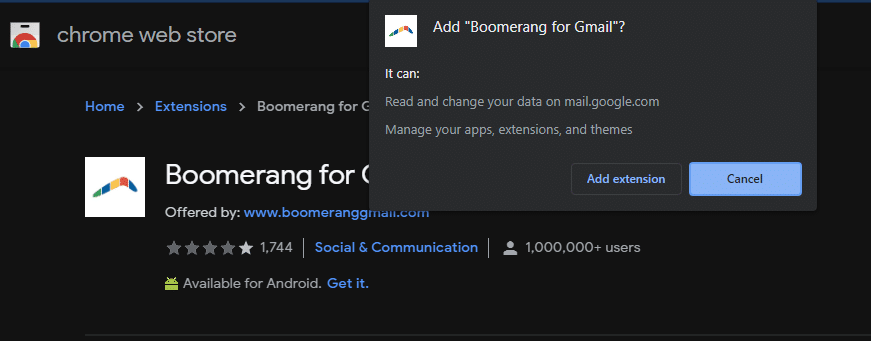
However, a lot of browser extensions require more comprehensive permissions. A common one is Read and change all your data on the websites you visit. This is required for everything from password managers to dark mode toggles to grammar-checking utilities.
Giving an extension this level of access is serious. Having complete control over the data on every website you visit means that an extension could inject malicious ads onto the page, track everything you’re doing, capture sensitive information that you type on secure sites like your bank, and similar.
Of course, not every extension that asks for this access will abuse it. But if an extension wanted to, it could perform nasty actions like this once you granted it access.
Extensions Can Become Dangerous in Different Ways
Sometimes, a trusted extension can go rogue and start acting against its users. There have been many cases of this happening.
For example, Hover Zoom was a once-popular Chrome extension that let you view full-sized images when you moused over them on a website. Eventually, people discovered that the app was tracking user data and sending it off to a remote server. The owner eventually removed it from the Web Store, but everyone who had trusted the extension felt betrayed.
In other instances, a once-trusted extension is sold to a shady developer. Developers of Chrome extensions have shared stories about being approached by spammy companies who offer to pay a lot of money to buy their extension. For example, the developers of the popular coupon code-finding extension Honey did an Ask Me Anything on Reddit back in 2014, where they mentioned that they had an offer from a data collection company to buy the extension for over six figures per month.
If they sell, the new owners inject tracking, ads, and other junk into the extension, then update it on the Chrome Web Store. Everyone already using that extension now has the compromised version, and Chrome doesn’t even let you know (unless an extension starts requiring new permissions).
It’s safe to assume that extensions from major companies aren’t going to abuse their privileges. For example, a Microsoft extension that lets you save webpages to OneNote is very unlikely to fall into the hands of crooks. But a random no-name extension is a target for this kind of behavior, especially once it starts enjoying some popularity.
Enterprises Can Monitor Extensions
While it’s always smart to stay on top of extensions on your own, these issues pose a particular threat to businesses. Having to manage what extensions are installed on dozens or hundreds of computers manually is inefficient.
Thankfully, Google and Microsoft provide tools for enterprise use in Chrome and Edge. IT staff in a company are able to reject extensions that require certain permissions, allow only specific extensions of their choosing, block certain extensions, or set up similar policies. Preventing these extensions from getting on computers in the first place is important for security.
See Google’s page on managing extensions for enterprise Chrome users and Microsoft’s page on enterprise Edge extension management to learn more.
Audit Your Browser Extensions Regularly
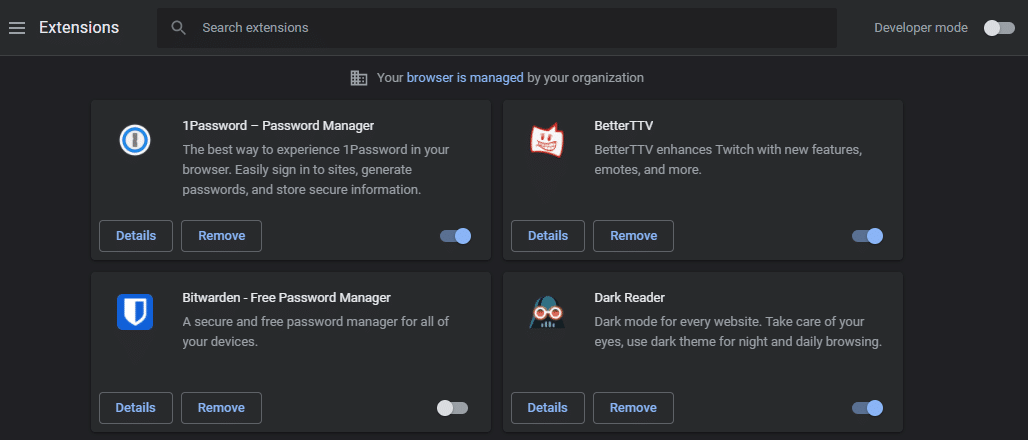
Whether an extension is dangerous from the beginning or is sold to a developer that ruins it, you have to be vigilant about what browser extensions you use. You should regularly check your list of installed extensions and make sure you still trust them all.
Open up their page on the Chrome Web Store (or equivalent for your browser) to check some details, like when it was last updated. It’s also smart to look at the recent reviews and see if people are complaining about shady behavior.
If you don’t trust an extension, disable or remove it from your browser. In Chrome, when you uninstall an extension, you’ll have the option to Report abuse, which you should do if it applies. Browser developers have safety measures in place to catch the worst extensions, but they aren’t perfect.
You should treat browser extensions like you treat desktop software or apps on your phone. If you don’t trust it—or the group who developed it—then you should avoid it. You access a lot of sensitive information in your browser, and letting a dozen random extensions you know little about snoop on all that info isn’t wise.
For more ways to stay safe, be aware of other browser security dangers.




