Simjacking is a growing threat that results in major problems for its victims. It’s important for you to understand how this attack works and what you can do to protect yourself from this type of account fraud.
What Is Simjacking?
Simjacking, also called SIM swapping, is a way for attackers to take over someone’s phone number through fraudulent means. You’re likely familiar with SIM cards, which are small cards inside a phone that allow it to communicate with the carrier network. Your phone number is tied to your SIM, allowing you to make calls and send texts.
In a simjacking attack, an attacker convinces your phone company to move your number to a SIM card that the criminal controls, allowing them to take over your number and everything associated with it.
The dangers of simjacking are clear: someone with access to your phone number will receive all your calls and text messages. They could use this to impersonate you and steal money from trusted contacts. A particular risk is the fraudster gaining access to any two-factor authentication (2FA) codes sent by text message.
You should also be aware that if your phone has an eSIM (an all-digital SIM that provides the same functionality without a physical card), this offers no additional protection from a simjacking attack. The effect is the same since the method involves deceiving your mobile carrier, and has nothing to do with your own SIM card.
How Does Simjacking Work?
While simjacking is a more complex attack than a standard phishing email, it’s not difficult to understand how it works.
First, the attacker gathers information about you so they can more convincingly pose as you to your phone company. This might involve browsing your social media pages to collect basic info that’s often used for security questions, like your mother’s maiden name or your high school’s mascot.
Alternatively, the attacker can use a phishing attack (perhaps SMS text message phishing) to trick you into handing over your account details. If you provide your login details for your mobile provider directly to the fraudster, they have what they need to impersonate you.
From there, simjacking takes advantage of the normal process of porting a phone number to a new device. This is something you’d walk through if you lost your phone and got a new one: you’ll need to ask your carrier to port your SIM to your replacement device. In a SIM swapping scheme, the attacker contacts your mobile provider (usually over the phone) and convinces them to move your number to a new SIM. They’ll lie and say that “you” lost your old phone, or similar.
If they’re successful, they have control over your phone number (you can’t use it anymore). From there, they can intercept any 2FA codes that are texted to your phone and use your phone number to reset the passwords for accounts they want to break into.
How to Stay Safe Against Simjacking
While simjacking is a frightening attack, since it happens with little to no input from you, you can take steps to shield yourself from it.
The first step is a general way to protect yourself against many digital attacks: be careful what you do and click online. Be aware of what you post on social media and how people could use it against you in ways like this. Never open a link in an email, text message, social media message, or similar, as that’s a common method of phishing.
The other methods are more focused on SIM swapping itself. If you have accounts that use SMS texts as a 2FA method, you should disable this in favor of a more secure form of two-factor authentication. For most people, we recommend authenticator apps like Duo Mobile or Microsoft Authenticator, which are not vulnerable to SIM swapping since they are device-based and not tied to your phone number.
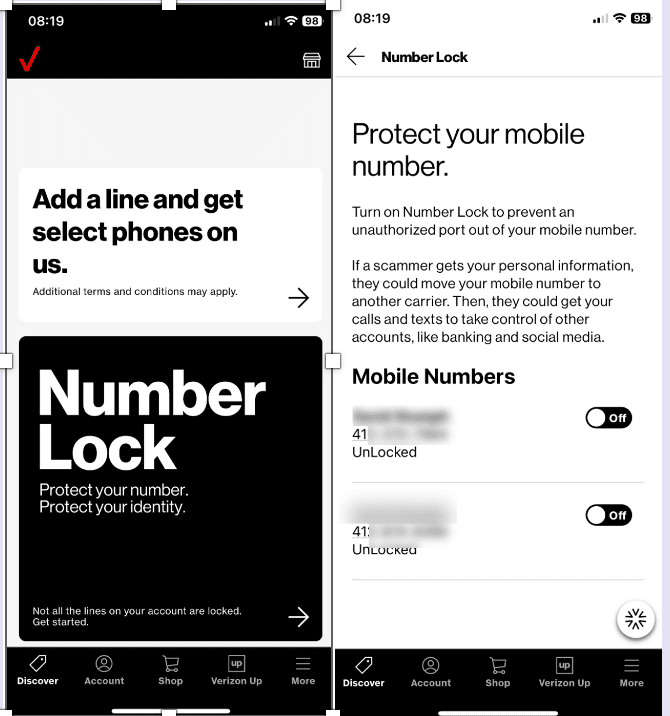
Since simjacking relies on your carrier being tricked, it’s also important to review the security options that your mobile carrier provides to protect against your number being ported fraudulently. For instance, Verizon provides a service called Number Lock that prevents your number from being moved to another device by protecting this procedure with a PIN.
Head to Settings > Number Lock > Choose number in the My Verizon app, call *611, or head to the Number Lock page on Verizon’s website. There, you can enable this option, which blocks requests to move your number until you deactivate it.
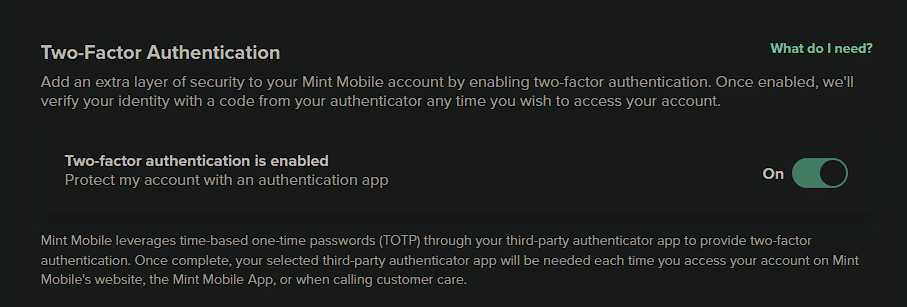
Regardless of whether your carrier offers an option like this specifically for number porting, you should activate other security settings to reduce the chance of attack. In particular, be sure to turn on two-factor authentication so that an attacker can’t log into your carrier’s website to initiate the attack. Some carriers also provide the option to require a secret passphrase when you contact them – this is a useful option to prevent others from impersonating you.
If security options are the only method of additional authentication, make up answers and store them in your password manager so others can’t guess them.
In the unfortunate case that simjacking happens to you, the first sign is typically that your phone number will stop working – you won’t be able to make or receive calls or texts. You might get a message from your carrier that your SIM has been ported.
If this happens, immediately contact your carrier, as they should be able to disable the fraudulent SIM. Then, you should make your contacts aware in case the impersonator tries to deceive them. You should also contact all your financial accounts and request a freeze. As possible, log into all your critical accounts, unlink the compromised phone number, and move them to a new email address,
Simjacking Is Nasty and Targeted
As we’ve seen, SIM swapping attacks are invasive and allow criminals to take over your digital accounts. As these attacks become more common, mobile companies will hopefully increase their protections so their staff know not to approve fraudulent swaps.
Until then, you should know about these schemes and how to stay safe. Make sure your mobile account has strong security, and don’t use SMS-based 2FA if at all possible. Other 2FA options, like authenticator apps, are more secure.
Using such apps is just one of the core security practices everyone should know.




