While two-factor authentication is a vital step for improving account security, you’ve likely noticed that there are a variety of options for this. But which are the best? It depends on the scenario and the balance of security and convenience you’re looking for.
Let’s consider some common forms of secondary authentication so you understand the security advantages and disadvantages of each.
How Two-Factor Authentication and Two-Step Authentication Differ
Two-factor authentication (2FA) and two-step authentication (2SA) are terms mistakenly used interchangeably by some people. While similar, they aren’t identical and have important security implications.
To understand the difference, we must consider what a factor is. In security, there are three main kinds of factors:
- Something you know: Any piece of private information, like a password or PIN.
- Something you have: Anything physical you have on your person.
- Something you are: A physical characteristic of your body.
When two methods of the same factor are used to verify a login, it’s two-step authentication because there are two steps of a single factor. Conversely, requiring info from two different factors is two-factor authentication.
Consider a high-security environment where a user is required to both scan their fingerprint and insert their ID badge to access a system. This is two-factor authentication, as it requires the badge (something they have) and the fingerprint (something they are). However, asking for security questions on top of a password is only two-step authentication, since both parts are something the user knows.
The strength of two-factor authentication comes from the fact that each type of authentication has its own strengths. Something you know (a password) can be stolen through social engineering, but unless the thief also has your phone or access to your person, your account remains protected.
With the basics explained, let’s look at the most common 2FA methods.
1. SMS or Email Messages
One of the simplest 2FA methods is send a text message to your phone, or an email to your registered address, with a randomized code. This is simple because everyone uses SMS texting and email, so there’s nothing additional to set up.
While better than nothing, this method is open to various kinds of attacks because SMS and email are not secure methods of messaging. SIMjacking, where an attacker fraudulently transfers your phone number to a new SIM card, allows them to steal your SMS codes. Email accounts are relatively easy to access via phishing.
2. Time-Based One-Time Passwords (OTP)
One-time passwords use an app like Microsoft Authenticator to generate a security code that changes regularly. Once you scan a QR code and add an account to the app, you don’t need a network connection to view your code.
While they require more setup since you need a dedicated app, OTP apps are generally the best balance of security and convenience. The security key is stored on the device, so it can’t be intercepted like a text or email can. And because the code changes so often, it’s near-impossible to guess.
OTP isn’t perfect, as it’s possible to clone the secret key and thus gain access to your codes. But the chance of this happening is low.
3. Push Notifications
Certain OTP apps allow you to tap a notification sent to your phone instead of entering a code. This allows you to allow or deny the request more quickly—though you need a network connection to receive them in the first place.
Besides the obvious advantage of convenience, these notifications also contain info about the login attempt (such as the general location and operating system). This makes it easier to confirm that you’re approving a legitimate request.
However, this convenience can have a dark side. Given the barrage of notifications many people get, it’s easy to gloss over the alert and confirm something that you didn’t mean to. So if you use this method, you must be vigilant during approvals.
Thankfully, OTP apps that support push notifications are starting to make changes to avoid this weakness. Both Duo Mobile and Microsoft Authenticator have rolled out “verified push”, which requires more thought to approve login attempts. With this option, instead of simply tapping “yes” to log in, you’ll need to enter a short code on your phone that’s displayed on the device you’re trying to log into.
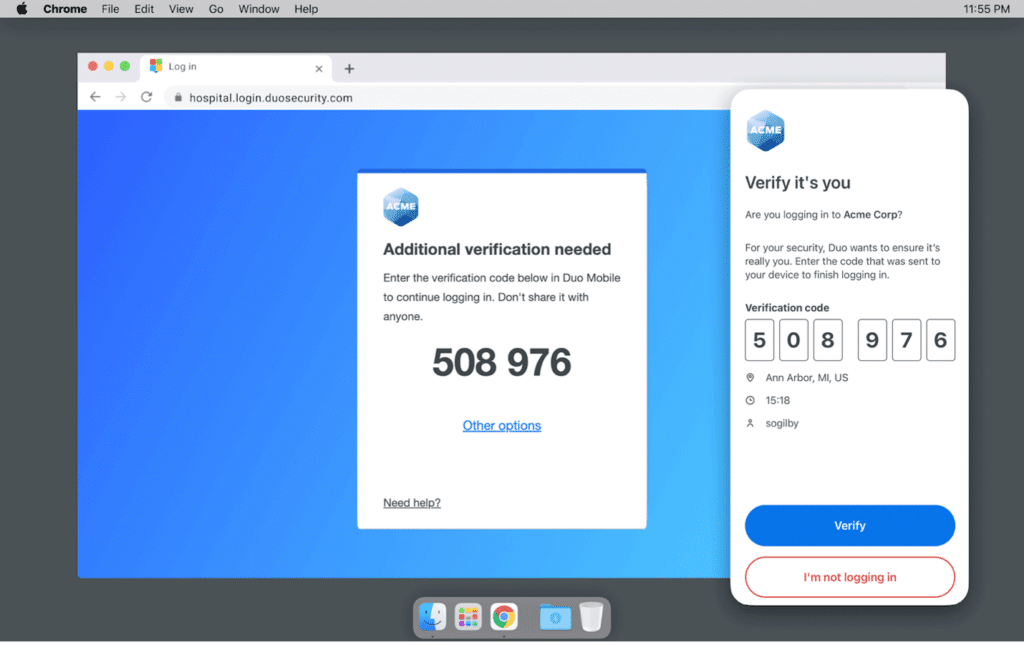
This prevents you from approving a login attempt by mistake by adding a short, but important, additional step. There’s also an “It’s not me” button that appears, allowing you to report malicious attempts to access your accounts.
4. Physical Security Keys
This method involves you carrying a small physical USB key (like a YubiKey) that you use to authenticate login requests. These offer strong security, since they are a physical item that can’t be intercepted via phishing or network breaches.
Because you have to register the key with each account you use them with, it can’t be phished—an attacker can’t set up a fake site to steal your key. The only way this method can be compromised is if you lose it or authenticate on a device you don’t trust.
However, this strong security also comes with usability drawbacks. Not all services support physical keys, and they come with a cost, unlike the above methods. If you forget the key at home, you’ve got a problem.
The USB form factor of each key is also a consideration. If you buy a YubiKey with USB-C to use with your phone, you’ll need an adapter or a different key to use it with your laptop that lacks USB-C ports. YubiKey sells keys that can authenticate by touching your device via NFC. While this works quite well, models supporting NFC are more expensive.
5. Biometrics
Biometrics refers to authenticating users using part of their body, such as a fingerprint, facial scan, voice recognition, or retinal scan. The major advantage of such methods is that they’re difficult to break into—it’s difficult to steal someone’s fingerprint or make a convincing copy of their face.
While biometrics are used in classified systems and as unlock methods on phones, they aren’t as common for 2FA. This is because the scanners that support them are expensive and often clunky—nobody is going to carry around a portable fingerprint scanner to log in.
6. Security Questions
One of the oldest 2SA methods is also the weakest. Security questions ask you to provide answers to prompts that, ostensibly, only you know the answers to.
The problem is that this information can be easy to find online. People can study your social media profiles to figure out your high school mascot or your grandmother’s name. Even worse are security questions with a set of predetermined answers to pick from.
You shouldn’t use security questions unless you’re forced to. In that case, we recommend entering a nonsense answer that you save in your password manager. This makes the security questions act as a second password, instead of being easily guessable.
Will We Need 2FA With Passkeys?
You might have seen some services asking you to use a passkey, which is an emerging method for authentication that gets around many of the disadvantages inherent to passwords. Passkeys use an authentication method on your device, such as your fingerprint or facial unlock, to sign directly into supported websites. This means that instead of having to have separate strong passwords for your Google and Microsoft accounts, you simply have to use the fingerprint unlock on your phone to sign into both.
No passwords means attackers can’t steal them, and since a passkey is created for a given site, you can’t take one login and apply it across sites. Passkeys growing in popularity will mean a smoother login experience for people and easier security for all, without any extra work.
Which 2FA Methods Do You Use?
We’ve taken a brief look at each major 2FA method available. While you’re often limited based on what the site offers, you should always check your options and choose the most secure method you’re comfortable with.
In most cases, that’s a one-time password app, perhaps with push notification support. If you’re serious about security and don’t mind carrying it around, a YubiKey is a great investment and is even more resistant to attack.
While you’re thinking about security, make sure to put other recommended security tips into practice, too.




